Even with improvements in radiation detector materials, the associated readout electronics may limit the ultimate performance of a measurement system. In recent years, digital pulse processors have added new capabilities to the conventional analog readout methods. Michigan has been at the vanguard of this revolution, with much of the fiducial work done by innovative graduate students, and further advanced throughout their professional careers. In this section, we highlight a recent project where the ADC has been redesigned to provide a secure measurement system for nuclear arms control. The full publication can be downloaded here.
Readout circuits fabricated in InGaP HBT technology, tested by a Network Analyzer for electrical performance.
A Secure Measurement Unit for an Inspection System Used in Nuclear Arms-control Verification |
I. INTRODUCTION
Verifying compliance with the terms of future arms control agreements may involve radiation measurements of the objects, such as neutron counting, or more commonly, through gamma ray spectral measurements. As described, the host party must certify that the measurement device meets not only the local facility security requirements, but also does not reveal sensitive information. On the other hand, the inspecting party must ensure that the measurement device produces results that will noninvasively authenticate the proffered object is as asserted. If a proposed authentication process acquires information that could be deemed by the host as sensitive, an information barrier must be included to block the inspecting party from that data. The security of the information barrier thus plays a rather critical role in treaty compliance negotiations.
Two general classes of authentication methods have evolved: attribute-based and template-based. In the attribute-based method, properties of the inspected object that will provide confidence in its authenticity are measured. Examples of such systems include the Controlled Intrusiveness Verification Technology (CIVET) , Trusted Radiation Attribute Demonstration System TRADS, Third Generation Attributes Measurement System 3G-AMS, Fieldable Nuclear Material Identification System FNMIS, and the UK-Norway Initiative UKNI.
In the template matching class, the object to be authenticated is compared to another device known to be authentic (i.e., the Master- or Golden-Copy). Systems such as Next Generation Trusted Radiation Identification System NG-TRIS and CONFIDANTE , among others, follow this paradigm. In an ideal case, authentication can be accomplished without revealing sensitive data by only looking at the differences from the template.
Some of the proposed systems require a gamma ray spectrum, as produced from an HPGe detector, and embed an information barrier in internal software. An example is the warhead verification concept proposed Vavrek that uses HPGe detectors to detect transmission nuclear resonance fluorescence gamma rays to achieve cryptographic warhead verification. The acquired gamma spectra may inadvertently reveal sensitive information, but an ADC that suppresses any secondary lines would harden this technique. Indeed, a natural concern of both the host and inspecting party is the vulnerability of any sensitive information residing internally. In our approach, we address these vulnerabilities by moving the information barrier into the digital measurement process. The idea is to avoid generating sensitive data, but retain only information needed for the verification process and ensure the process is secure against side-attacks.
II. Successive Approximation (SAR) Assisted Pipeline ADC
We modified the common SAR-assisted pipeline ADC architecture to both embed an information barrier and to secure the ADC from side-channel attack.
The prototype 14-bit SMU is implemented in 65 nm CMOS and occupies 0.103 mm2. The prototype is packaged in a 56-pin 8×8 mm QFN package. A bootstrapped sampling circuit lowers sampling distortion. The first stage CDAC, C-SAR logic, comparator preamp, and the first comparator comprise the first sub-ADC that implements the information barrier. Stage two CDAC, SAR logic, and the second comparator comprise the second sub-ADC. Two custom-designed printed circuit boards support the use and evaluation of the SMU.
A. Radioisotope Testing
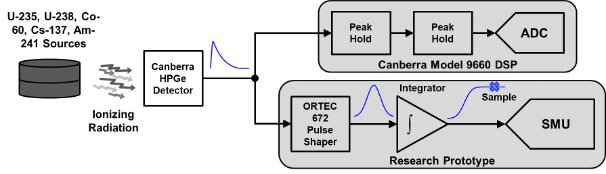
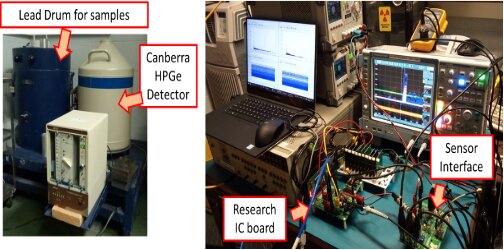
We tested the SMU prototype using combination of radioisotopes to check its ability to measure different spectra. This test was run without any restrictive information barrier. The U-235, U-238, Co-60, Cs-137 and Am-241 sources provide energy spectra with unique peaks. The sources were placed within the lead housing that contained a Canberra HPGe detector, and a Canberra 20002C preamplifier provided the analog input for our testing.
To evaluate the accuracy of the research prototype SMU, the preamplifier output signal was split into two paths, one path feeding the prototype SMU and the other to a commercial Canberra 9660 unit. An Ortec 972 Pulse Shaper followed by a custom-designed integrator printed circuit board fed the prototype SMU integrated circuit.
The figure below shows the measured spectra from both the prototype SMU and the commercial Canberra 9660 DSP system. The SMU spectra is comparable to its commercial counterpart in that all peaks from the U-235, U-238, Co-60, Cs-137, and Am-241 are sources clearly visible. A Gaussian fit to the Cs-137 peak counts yielded a Full Width at Half-Maximum (FWHM) of 2.16 keV, slightly worse than the commercial system’s FWHM of 1.41 keV.
To test the effectiveness of the information barrier, a spectrum from the U-235, U-238, Co-60, Cs-137, and Am-241 sources was acquired with restricting the input signals to lie within small windows around the U-235 (185.90 keV), Cs-137 (662.16keV), and U-238 (1001.91 keV) peaks. The figure below plots the measured spectrum over a 300 s acquisition. As intended, the SMU only digitized signals within the allowed range. Note that some Compton background counts from higher energy sources are captured within the allowable range.
III. Conclusion
In order to mitigate security vulnerabilities during verification tasks and to enhance the possibility of more intrusive treaty inspections, we moved the information barrier into the digitization process so that sensitive data was never created. This eliminates vulnerabilities present in other verification approaches that acquire the data and then delete it later in an information barrier. A 14-bit prototype, secure, custom-ADC provided HPGe energy resolution comparable to an analog commercial setup but adds an intrinsic information barrier and resilience against side-channel attacks.
Note that moving the information barrier within the digitization process may not be possible for verification scenarios in which sensitive data is required in order to calculate derived quantities, such as ratios (e.g., Pu-240/Pu-239), that are not sensitive. Similarly, the measured counts in an allowable region may contain Compton scattered events from within prohibited regions. For the complex spectra expected in practice, we do not envision this to be a significant security issue, but it should be considered. Finally, one area that deserves further exploration, unrelated to the passive inspection scenario, is the ability to enhance signal throughput by adaptively culling uninteresting data during acquisition. This could be helpful for interrogation scenarios in which the interesting data are a small fraction of the total.